By Asheer Malhotra.
Analysis of a recently discovered preliminary variant of ObliqueRAT in this post presents insights into the evolution of this threat. Analyses of the key similarities and differences between the two campaigns of ObliqueRAT and CrimsonRAT show us the changes in tactics and techniques of the attackers used to continue attacks while trying to bypass detections. This campaign also shows us that while network-based detection is important, it can be complemented with system behavior analysis and endpoint protections for additional layers of security.
The maldocs have been known to have seemingly benign file names in the wild such as:
These file names indicate that the maldocs may be targeted towards specific individuals as part of a targeted distribution campaign. The initial infection vector of this threat is most likely email based with the body of the malicious email containing the password required to open the maldocs.
The second-stage binary (ObliqueRAT) contains the following features:
Sysinfo gathered by the RAT:
The sysinfo gathered by the implant is then put together as a single string with the character ">" used as a delimiter.
Format used:
(_variable_ = used for depicting a variable value)
_ComputerName_>_UserName_>Windows _version-string_>_implant-name-on-disk_>_OS-bitness_>_Dump_dir_files_exist_>_hardcoded_implant_version_number_>
E.g.
DESKTOP-SCOTTPC>jon>Windows 10>sgrmbrokr>64 bits>Yes>5.2>
Although the implant gathers the system information initially, it only sends this information out if it receives a specific command code from the C2. The implant also performs anti-infection checks before it fully activates itself on the endpoint.
The usernames blacklisted by the implant are:
A similar check is done for the computer name as well. The list of computer name values blacklisted by the implant are:
The anti-infection checks may have been implemented to:
On connection, the implant receives a command code from the C2 that corresponds to the capability the implant is supposed to execute next on the endpoint. Also, everytime the implant receives a command from the C2 it sends back an acknowledgement message to the C2 indicating that it has received the command code.
The acknowledgment sent to the C2 is always the keyword "ack".
The command codes, supporting command data (both sent by the C2) and capability description are detailed below.
This command code is used to find files and record file sizes in KB for files specified by a specific folder or file path. The data gathered by the implant is in format:
(_variable_ = used for depicting a variable value)
_filepath_<_size_in_KB_;_filepath_<_size_in_KB_;
E.g.
pony.txt<4;bigpony.txt<100;
Send the already gathered system information (sysinfo) described previously to the C2 server for fingerprinting the infected host.
This command is aimed to trigger the implant to discover the category of various drives on the endpoint. The drives to be checked for are listed as hardcoded drive letters in the implant:
The drive types for the drives checked on the system are represented textually by the implant using the following keywords:
The data sent out for this command is in format:
(_variable_ = used for depicting a variable value)
_drive-letter_>_Drive-type_|_drive-letter_>_Drive-type_|
E.g.
C:>Hard Drive|D:>CD Drive|
Receive a target filename and ZIP filename from the C2server. Create a new ZIP file with the name provided in the %temp% directory and add the target file to it. Once done, send the contents of the ZIP file to the C2 server.
The ZIP file is subsequently deleted from the endpoint after exfiltration.
The implant also records the target filename that has been exfiltrated (in ZIP form) from the endpoint to a log file called: %temp%\lgb
Variant of command code "4." The difference here is that the implant doesn't require a different ZIP file name from the C2 it simply uses the name of the target filename and creates a ZIP file.
E.g. if the target file name is "abc.txt" then the ZIP file name is "abc.txt.zip"
Accept a folder path from the C2 server, recursively find all files residing in the folders and ZIP them up into a ZIP file with the same name as the folder path specified by the C2. (The ZIP file is created in the operating directory of the implant). This ZIP file is then exfiltrated by the implant to the C2 and subsequently deleted.
Variant of command code ="5". The difference here is that implant accepts only a foldername and recursively calculates the file sizes and builds the list of filepaths and filesizes in the same format:
_filepath_<_filesize_;_filepath_<_filesize_;_filepath_<_filesize_;
Execute given command line on the endpoint with a high priority (The output of the command executed on the endpoint is not sent back to the C2 though).
This command is used by the implant to write a file sent by the C2 to the infected endpoint. To achieve this functionality the implant recvs the following info from the C2 server:
Backup the contents of the lgb log file to another file. The backup is done
From = %temp%\lgb
To = %temp\lgb2
The implant reads the lgb log file character by character and writes it to the lgb2 file. On encountering a newline character, the newline is replaced by "*\n" instead.
Once the backup is done the implant will remove the "lgb" log file and then rename the lgb2 file back to "lgb" (Convoluted backup mechanism used here).
Rename a file to a new name provided by the C2.
This command is used to gather the list of running processes on the system, record this information to a log file and exfiltrate the contents of the log file. Once the log file has been sent to the C2 it is removed from the endpoint.
Log filepath used = C:\ProgramData\a.txt
Log file format =
Running Processes
<process_image_name>
<process_image_name>
<process_image_name>
.
.
.
Stop execution of implant on the endpoint without removing persistence from Star-tUp folder.
Restart the socket connection to the C2.
Find all processes by the name specified by the C2 and terminate them.
This command code is used to trigger a recursive search sweep of one or more directories specified by the C2 server. This sweep is done to verify the presence of files specified by a filename. The data specified by the C2 is:
Any files matching the specified criteria are logged into the file C:\ProgramData\auto.txt
Format:
_folderpath_>_filename1_,_filename2_,_filenameN_<_file-extn1_,_file-extn2_,_file-extnN_
E.g.
If the command data sent by the C2 is:
c:\dummy>pony.txt,blah.exe<txt,exe
Then if these files exist, the log file ("auto.txt") will contain:
c:\dummy\pony.txt
c:\dummy\blah.exe
The log file (auto.txt) is then read and the contents are sent to the C2 followed by its deletion.
This command is used to delete (remove) a file specified by the C2 server from the endpoint.
Keywords used by the RAT during communication are:
ObliqueRAT Variant #0 EXE:
Persistence Component EXE:
If specific file markers exist in the dropper's binary file on disk: (Markers used= "***")
If the markers do not exist then it will package its components into a new copy of itself:
Shortcut created: %userprofile%\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\script.lnk
This is because of the following factors:
An example of a maldoc (from December 2019) observed distributing the CrimsonRAT malware is:
The CrimsonRAT sample dropped by the maldoc is:
This campaign shows a threat actor conducting a targeted distribution of maldocs similar to those utilized in the distribution of CrimsonRAT. However, what stands out here is that the actor is now distributing a new family of RATS. Although it isn't technically sophisticated, ObliqueRAT consists of a plethora of capabilities that can be used to carry out various malicious activities on the infected endpoint. The fact that the maldocs are password protected (and that the ObliqueRAT implant consists of probable anti-analysis techniques) indicates the attackers' intent to hide the malicious activities of the infection from an analyst. This campaign started in January 2020 and is still ongoing. This campaign also shows us that while network-based detection is important, it must be complemented with system behavior analysis and endpoint protections.
Ways our customers can detect and block this threat are listed below.
Advanced Malware Protection (AMP) is ideally suited to prevent the execution of the malware detailed in this post. Below is a screenshot showing how AMP can protect customers from this threat. Try AMP for free here.
Cisco Cloud Web Security (CWS) or Web Security Appliance (WSA) web scanning prevents access to malicious websites and detects malware used in these attacks.
Email Security can block malicious emails sent by threat actors as part of their campaign.
Network Security appliances such as Next-Generation Firewall (NGFW), Next-Generation Intrusion Prevention System (NGIPS), and Meraki MX can detect malicious activity associated with this threat.
Threat Grid helps identify malicious binaries and build protection into all Cisco Security products.
Umbrella, our secure internet gateway (SIG), blocks users from connecting to malicious domains, IPs, and URLs, whether users are on or off the corporate network.
Additional protections with context to your specific environment and threat data are available from the Firepower Management Center.
Open Source Snort Subscriber Rule Set customers can stay up to date by downloading the latest rule pack available for purchase on Snort.org.
The following IOCs are related to this threat:
Dropper (for Variant #0)
2nd Stage Malicious EXEs
Persistence Component
Mutexes Created by 2nd Stage EXEs:
C2 IP Addresses and URLs:
Next Stage Malicious ZIPs & EXEs
![]()
- Cisco Talos has observed a malware campaign that utilizes malicious Microsoft Office documents (maldocs) to spread a remote access trojan (RAT) we're calling "ObliqueRAT."
- These maldocs use malicious macros to deliver the second stage RAT payload.
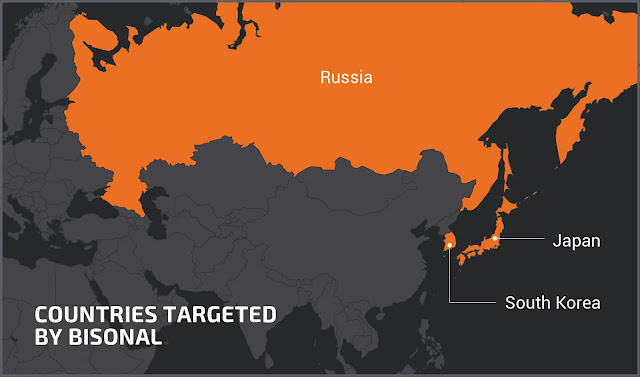
- This campaign appears to target organizations in Southeast Asia.
- Network based detection, although important, should be combined with endpoint protections to combat this threat and provide multiple layers of security.
What's New?
Cisco Talos has recently discovered a new campaign distributing a malicious remote access trojan (RAT) family we're calling "ObliqueRAT." Cisco Talos also discovered a link between ObliqueRAT and another campaign from December 2019 distributing CrimsonRAT sharing similar maldocs and macros. CrimsonRAT has been known to target diplomatic and government organizations in Southeast Asia.How did it work?
This RAT is dropped to a victim's endpoint using malicious Microsoft Office Documents (maldocs). The maldocs aim to achieve persistence for the second-stage implant that contains a variety of RAT capabilities, which we're calling "ObliqueRAT." In this post, we illustrate the core technical capabilities of the maldocs and the RAT components including:- The maldocs based infection chain
- A variant distributed using a dropper EXE.
- Detailed capabilities and command codes of the RAT implant (2nd stage payload).
- Communication mechanisms used.
So what?
This malware is an example of how a simple, yet effective RAT, is used to implement a wide variety of malicious capabilities. Key capabilities of ObliqueRAT include:- Ability to execute arbitrary commands on an infected endpoint.
- Ability to exfiltrate files.
- Ability to drop additional files.
- Ability to terminate process on the infected endpoint etc.
Analysis of a recently discovered preliminary variant of ObliqueRAT in this post presents insights into the evolution of this threat. Analyses of the key similarities and differences between the two campaigns of ObliqueRAT and CrimsonRAT show us the changes in tactics and techniques of the attackers used to continue attacks while trying to bypass detections. This campaign also shows us that while network-based detection is important, it can be complemented with system behavior analysis and endpoint protections for additional layers of security.
Analysis of Maldocs
Initial Infection Vector
This threat arrives on the endpoint in the form of malicious Microsoft Word documents. The malicious documents (maldocs) prompt the end-user for a password to view the contents of the maldocs. The malicious VB script in the maldocs is activated once the user enters the correct password for the document.The maldocs have been known to have seemingly benign file names in the wild such as:
- Company-Terms.doc
- DOT_JD_GM.doc
These file names indicate that the maldocs may be targeted towards specific individuals as part of a targeted distribution campaign. The initial infection vector of this threat is most likely email based with the body of the malicious email containing the password required to open the maldocs.
Malicious VBA Analysis
Once opened, the maldoc activates a malicious VBA script that performs the following malicious activities:- Extracts the contents of a form/textbox.
- This content consists of an MS Windows binary embedded as a character representation of the binary's bytes delimited using a specific character (e.g. "O" used as a delimiter).
- The malicious binary is extracted from the maldoc by the VBA script and dropped on the endpoint to the location:
C:\Users\Public\sgrmbrokr.doc - The file is consequently renamed to an exe : C:\Users\Public\sgrmbrokr.exe
- The malicious VBScript then creates a shortcut in the currently logged in user's Start-Up directory to achieve persistence across reboots for the malicious executable (MZ) written to the file system in previous steps. The shortcut created is:
%userprofile%\\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\saver.url - Once the shortcut is created the VBScript stops execution without executing the actual second-stage payload (ObliqueRAT).
Delimited Malicious MZ embedded in maldoc highlighted.
Malicious VBA script in madocs
Second-stage payload analysis: ObliqueRAT
The second-stage binary (ObliqueRAT) contains the following features:
- RAT capabilities (detailed below).
- Ability to communicate with the command and control server (C2) to obtain command codes and send back executed command outputs.
Threat Grid detects this implant as malicious.
Threat Grid behavioral indicators for the implant.
Mutex Creation
The RAT ensures that only one instance of its process is running on the infected endpoint at any given time by creating and checking for a mutex named "Oblique". If the named mutex already exists on the endpoint then the RAT will stop executing until the next login of the infected user account.Mutex creation by implant
Gather initial system fingerprint
Once the malware has created the named mutex, it attempts to gather an initial fingerprint of the system to identify the system. This information is then sent to the operating C2 to fingerprint the system to decide which commands to send next.Sysinfo gathered by the RAT:
- Computer Name.
- Current User Account Name.
- Windows operating system (OS) version in the form of a textual representation:
- XP
- XP SP2
- Vista
- 7
- 8
- 8.1
- 10
- OS bitness i.e.
- 64 bits
- 32 bits
- Directory & File Check: A unique feature of the RAT is that it looks for the presence of a specific directory and all files residing inside it. The directory path (folderpath) is hardcoded in the RAT: C:\ProgramData\System\Dump.
If this directory is present on the infected system then the RAT sends the keyword "Yes" to its C2 and "No" otherwise.
- Another hard coded value from the implant "5.2" is sent to the C2. (May indicate version number of the implant)
The sysinfo gathered by the implant is then put together as a single string with the character ">" used as a delimiter.
Format used:
(_variable_ = used for depicting a variable value)
_ComputerName_>_UserName_>Windows _version-string_>_implant-name-on-disk_>_OS-bitness_>_Dump_dir_files_exist_>_hardcoded_implant_version_number_>
E.g.
DESKTOP-SCOTTPC>jon>Windows 10>sgrmbrokr>64 bits>Yes>5.2>
Although the implant gathers the system information initially, it only sends this information out if it receives a specific command code from the C2. The implant also performs anti-infection checks before it fully activates itself on the endpoint.
Anti-Infection Checks
Another interesting feature in the implant is that after it gathers the preliminary system information for fingerprinting, it performs a series of checks against the user and computer name it has obtained to identify an endpoint or user account it must avoid its execution on/for. If any of the values from its blacklist match the current user/computer name, it simply stops its execution.The usernames blacklisted by the implant are:
- John
- Test
- Johsnson
- Artifact
- Vince
- Serena
- Lisa
- JOHNSON
- VINCE
- SERENA
A similar check is done for the computer name as well. The list of computer name values blacklisted by the implant are:
- JOHN
- TEST
Blacklisted user & computer names in the implant
The anti-infection checks may have been implemented to:
- Avoid successful execution of the implant on a Sandbox based detection system (Anti-Analysis Technique) OR
- Prevent execution of the implant in the attackers' test environment.
RAT command codes and functionalities
The implant then connects to its C2 server using hardcoded values of its IP Address and Port Number.Implant connecting to hardcoded C2 server.
On connection, the implant receives a command code from the C2 that corresponds to the capability the implant is supposed to execute next on the endpoint. Also, everytime the implant receives a command from the C2 it sends back an acknowledgement message to the C2 indicating that it has received the command code.
The acknowledgment sent to the C2 is always the keyword "ack".
"ack" sent to the C2 as an acknowledgment
The command codes, supporting command data (both sent by the C2) and capability description are detailed below.
Command Code = "5" Command Data = <filename or folderpath>
(_variable_ = used for depicting a variable value)
_filepath_<_size_in_KB_;_filepath_<_size_in_KB_;
E.g.
pony.txt<4;bigpony.txt<100;
Command Code = "0" Command Data = None
Implant sending initial sysinfo to its C2 server.
Command Code = "1" Command Data = None
- A:
- B:
- C:
- D:
- E:
- F:
- G:
- H:
- I:
- J:
- K:
- L:
The drive types for the drives checked on the system are represented textually by the implant using the following keywords:
- Unknown
- Removable Drive
- Hard Drive
- Network Drive
- CD Drive
- RAM Disk
The data sent out for this command is in format:
(_variable_ = used for depicting a variable value)
_drive-letter_>_Drive-type_|_drive-letter_>_Drive-type_|
E.g.
C:>Hard Drive|D:>CD Drive|
Drive letters and identification strings in the implant.
Command Code ="4" Command Data=<filename> & <zip_file_name>
The ZIP file is subsequently deleted from the endpoint after exfiltration.
The implant also records the target filename that has been exfiltrated (in ZIP form) from the endpoint to a log file called: %temp%\lgb
Log file containing the list of files exfiltrated from the endpoint.
Command Code ="4a" or "4e" Command Data=<target filename>
E.g. if the target file name is "abc.txt" then the ZIP file name is "abc.txt.zip"
Command Code ="6" Command Data=<folder path>
Command Code ="3" Command Data=<foldername>
_filepath_<_filesize_;_filepath_<_filesize_;_filepath_<_filesize_;
Command Code ="7" Command Data=<command_line>
Sample command executed by the implant on the endpoint.
Command Code ="8" Command Data=<filename> , <filesize> & <file_contents>
- Path of the file to be written to on disk.
- Size of the file to be being sent by the C2.
- Contents of the file to be written to disk.
Command Code ="backed" Command Data= None
From = %temp%\lgb
To = %temp\lgb2
The implant reads the lgb log file character by character and writes it to the lgb2 file. On encountering a newline character, the newline is replaced by "*\n" instead.
Once the backup is done the implant will remove the "lgb" log file and then rename the lgb2 file back to "lgb" (Convoluted backup mechanism used here).
Command Code ="rnm" Command Data= <old_filename> & <new_filename>
File rename capability of the implant.
Command Code ="tsk" Command Data= None
Log filepath used = C:\ProgramData\a.txt
Log file format =
Running Processes
<process_image_name>
<process_image_name>
<process_image_name>
.
.
.
Process list snippet written to log file by the implant.
Command Code ="exit" Command Data= None
Command Code ="restart" Command Data=None
Command Code ="kill" Command Data=<process_name>
The implant's capability to terminate processes running on the endpoint.
Command Code ="auto" Command Data= Custom
- Folder path(s) to find files in.
- File name(s) to find.
- File extension(s) to find files.
Any files matching the specified criteria are logged into the file C:\ProgramData\auto.txt
Format:
_folderpath_>_filename1_,_filename2_,_filenameN_<_file-extn1_,_file-extn2_,_file-extnN_
E.g.
If the command data sent by the C2 is:
c:\dummy>pony.txt,blah.exe<txt,exe
Then if these files exist, the log file ("auto.txt") will contain:
c:\dummy\pony.txt
c:\dummy\blah.exe
The log file (auto.txt) is then read and the contents are sent to the C2 followed by its deletion.
Command Code ="rht" Command Data= <filepath>
RAT(Implant's) Communication Mechanisms
ObliqueRAT utilizes the ws2_32.dll library to communicate with its C2. This library is used to implement the core socket libraries supported by MS Windows.Keywords used by the RAT during communication are:
- "ack\0" = Acknowledgment of the command code received as well as an indicator of successful command execution.
- "nak\0" = Indicates failure to execute functionality without providing reason for failure to the C2.
Variant #0 - ObliqueRAT
Cisco Talos also discovered another variation of the ObliqueRAT attack distributed via a malicious dropper. The malicious dropper contains 2 EXEs embedded in it that will be dropped to disk during execution to complete the infection chain. The initial distribution vector of this dropper is currently unknown.Variant #0 Artifacts:
Dropper EXE:- 4a25e48b8cf515f4cdd6711a69ccc875429dcc32007adb133fb25d63e53e2ac6
ObliqueRAT Variant #0 EXE:
- 9da1a55b88bda3810ccd482051dc7e0088e8539ef8da5ddd29c583f593244e1c
Persistence Component EXE:
- ad17ada0171b9e619000902e62b26b949afb01b974a65258e4a7ecd59c248dba
Variant #0 Dropper Analysis
The dropper consists of one EXE with another two additional EXEs embedded in it. During execution the dropper will perform the following activities:If specific file markers exist in the dropper's binary file on disk: (Markers used= "***")
- If the markers exist then read the data between the markers (there will be 2 such markers for 2 embedded EXEs) and write it to files on disk:
- C:\Users\Public\Video\hrss.exe
- C:\Users\Public\Video\lphsi.exe
- Execute these files using the ShellExecute API.
If the markers do not exist then it will package its components into a new copy of itself:
- Look for files named "a.exe" and "b.exe" in the current working directory and read their contents into memory.
- Rename itself (the dropper) to "fin.exe".
- Append to itself (fin.exe) the magic markers specified ("***") and the contents of "a.exe" and "b.exe" thereby completing the packing process.
ObliqueRAT component Functionalities (lphsi.exe)
The ObliqueRAT sample dropped by the dropper has the same capabilities as the ObliqueRAT sample discussed above. There is a slight variation though (discussed in the comparison section below).Persistence Module (hrss.exe)
The 2nd EXE (hrss.exe) executed by the dropper is used only to establish persistence for the ObliqueRAT sample (lphsi.exe). This is done by creating a shortcut in the currently logged in user's Start-Up directory to execute ObliqueRAT whenever the user logs into the infected endpoint.Shortcut created: %userprofile%\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\script.lnk
Malicious shortcut (script.lnk) used for persistence.
Variant #0 Comparison
Variant #0 (9da1a55b88bda3810ccd482051dc7e0088e8539ef8da5ddd29c583f593244e1c) discovered by Cisco Talos looks like a preliminary version of the ObliqueRAT attack detailed in this post (37c7500ed49671fe78bd88afa583bfb59f33d3ee135a577908d633b4e9aa4035).This is because of the following factors:
- Variant #0 has an earlier compile time of 04/11/2019 12:12:04 UTC while the ObliqueRAT implant detailed in this post has a later compile time of 27/11/2019 08:40:10 UTC.
- Although the hardcoded version number of both the implants is "5.2", variant #0 contains an additional feature where, if the implant fails to connect to the C2 server it will display any of two Message Boxes consisting of:
Title = scokerr
Text = sockerror
and
Title = grace
Text = grace
Related campaigns: CrimsonRAT vs. ObliqueRAT
The malicious VBA Scripts in the maldocs discovered by Talos semantically resemble a previously observed maldoc distribution campaign (from 2019) delivering another .NET based RAT family popularly known as CrimsonRAT. CrimsonRAT has been known to target organizations in Southeast Asia.An example of a maldoc (from December 2019) observed distributing the CrimsonRAT malware is:
- 965b90d435c1676fa78cdce1eee2ec70e3194c0e4f0d993bc36bfd9f77697969
The CrimsonRAT sample dropped by the maldoc is:
- 98894973a86aa01c4f7496ae339dc73b5e6da2f1dbcd5fe1215f70ea7b889b85
Similarities Between the Two Campaigns
This CrimsonRAT maldoc although not password protected (as in the case of the maldocs containing ObliqueRAT) contains the following similarities w.r.t the ObliqueRAT maldocs:- Similar VB variable naming conventions for filenames, folder names, ZIP file names:
E.g.
The ObliqueRAT VBScripts use variables named:
file_Salan_name, fldr_Salan_name, zip_Salan_file
while the CrimsonRAT VBScripts use variables named:
file_Allbh_name, fldr_Allbh_name, zip_Allbh_file - Similar decoding technique for the next stage payload:
Both sets of VBScripts extract the embedded next stage payload from a form (textbox) where the bytes of the next stage payload are character representations (of decimal numbers) delimited by a specific character.
Differences Between the Two Campaigns
- The CrimsonRAT maldocs drop the next stage payload to a ZIP file (E.g. %allusersprofile%\intaRD\thnaviwa.zip) on the filesystem.
However the ObliqueRAT maldocs drop the RAT payload directly to a file named:
C:\Users\Public\sgrmbrokr.exe
- As mentioned above, the CrimsonRAT maldocs drop a malicious ZIP file on the disk first and then extract the EXE within the archive file. This malicious EXE (.NET based CrimsonRAT) is then executed on the infected endpoint.
The ObliqueRAT maldocs however simply drop the malicious EXE (ObliqueRAT EXE) directly on the filesystem, create a shortcut in the infected user's StartUp folder. The EXE is not executed and the malware relies on the user to re-login for the ObliqueRAT infection to trigger.
ObliqueRAT VBA (Left) vs CrimsonRAT VBA (Right) code
Conclusion
This campaign shows a threat actor conducting a targeted distribution of maldocs similar to those utilized in the distribution of CrimsonRAT. However, what stands out here is that the actor is now distributing a new family of RATS. Although it isn't technically sophisticated, ObliqueRAT consists of a plethora of capabilities that can be used to carry out various malicious activities on the infected endpoint. The fact that the maldocs are password protected (and that the ObliqueRAT implant consists of probable anti-analysis techniques) indicates the attackers' intent to hide the malicious activities of the infection from an analyst. This campaign started in January 2020 and is still ongoing. This campaign also shows us that while network-based detection is important, it must be complemented with system behavior analysis and endpoint protections.
Coverage
Ways our customers can detect and block this threat are listed below.
Advanced Malware Protection (AMP) is ideally suited to prevent the execution of the malware detailed in this post. Below is a screenshot showing how AMP can protect customers from this threat. Try AMP for free here.
Cisco Cloud Web Security (CWS) or Web Security Appliance (WSA) web scanning prevents access to malicious websites and detects malware used in these attacks.
Email Security can block malicious emails sent by threat actors as part of their campaign.
Network Security appliances such as Next-Generation Firewall (NGFW), Next-Generation Intrusion Prevention System (NGIPS), and Meraki MX can detect malicious activity associated with this threat.
Threat Grid helps identify malicious binaries and build protection into all Cisco Security products.
Umbrella, our secure internet gateway (SIG), blocks users from connecting to malicious domains, IPs, and URLs, whether users are on or off the corporate network.
Additional protections with context to your specific environment and threat data are available from the Firepower Management Center.
Open Source Snort Subscriber Rule Set customers can stay up to date by downloading the latest rule pack available for purchase on Snort.org.
AMP Detections
AMP detects the ObliqueRAT implants as follows:ObliqueRAT AMP detection
ObliqueRAT variant #0 AMP detection
Indicators Of Compromise (IOCs)
The following IOCs are related to this threat:
ObliqueRAT
Maldocs- 057da080ae0983585ae21195bee60d82664355a7fd78c25f21791b165c250212
- dfad2a80dac91e7703266197ebbf5d67ef77467ab341dd491ad25d92d8118cac
Dropper (for Variant #0)
- 4a25e48b8cf515f4cdd6711a69ccc875429dcc32007adb133fb25d63e53e2ac6
2nd Stage Malicious EXEs
- ObliqueRAT - 37c7500ed49671fe78bd88afa583bfb59f33d3ee135a577908d633b4e9aa4035
- Variant #0 - 9da1a55b88bda3810ccd482051dc7e0088e8539ef8da5ddd29c583f593244e1c
Persistence Component
- ad17ada0171b9e619000902e62b26b949afb01b974a65258e4a7ecd59c248dba
Mutexes Created by 2nd Stage EXEs:
- "Oblique"
C2 IP Addresses and URLs:
- 185[dot]117.73.222:3344
CrimsonRAT
Maldocs- 965b90d435c1676fa78cdce1eee2ec70e3194c0e4f0d993bc36bfd9f77697969
Next Stage Malicious ZIPs & EXEs
- 3671b7ed9f67098d2a534673ed9ff46e90c03269c0bdd9b6f39ae462915ecdcb [ZIP]
- 2911a3da2299817533ca27a0d44c8234fdf9ecd0a285358041da245581673d6f [ZIP]
- 98894973a86aa01c4f7496ae339dc73b5e6da2f1dbcd5fe1215f70ea7b889b85 [exe]
- e436be68cdbdb7ea20e5640ad5fa5eca1da71edb9943c3bde446b4c75dacfbd0 [exe]