Vulnerabilities discovered by Cory Duplantis and Ali Rizvi-Santiago of Cisco Talos.
Cisco Talos is disclosing several vulnerabilities discovered in Atlantis Word Processor. Atlantis Word Processor is a portable word processor that is also capable of converting any TXT, RTF, ODT, DOC, WRI, or DOCX document into an eBook in the ePub format.
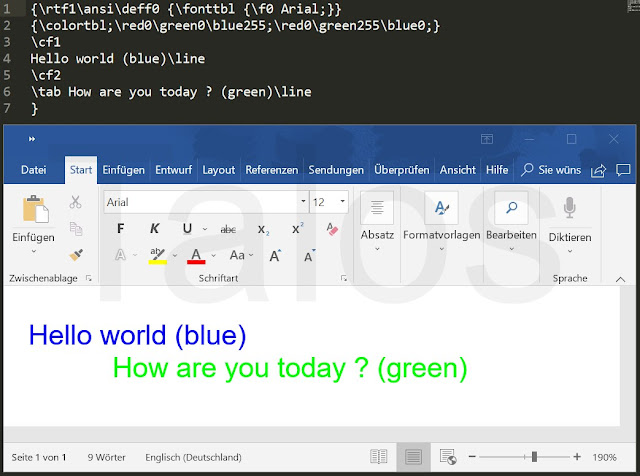
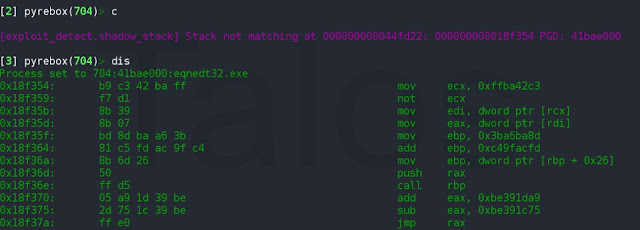
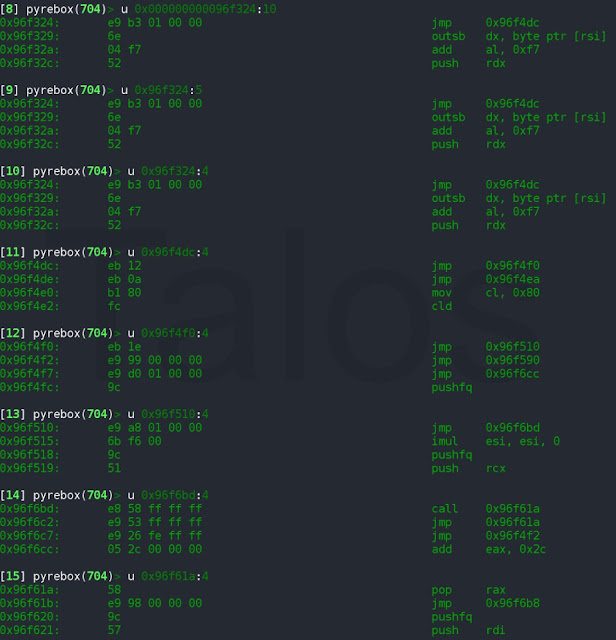
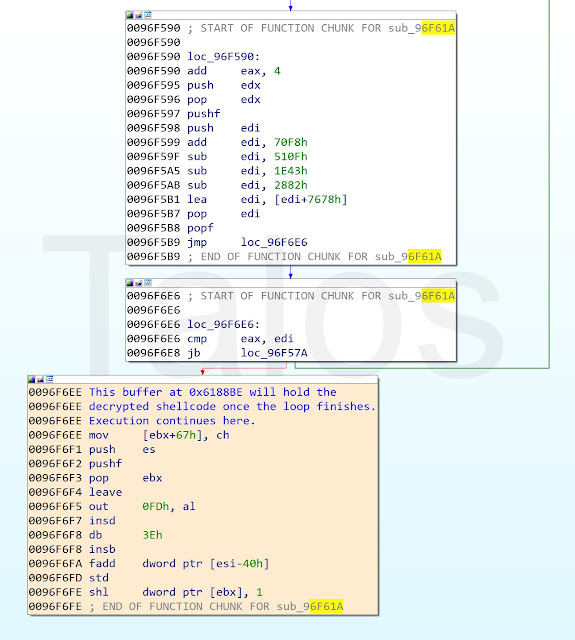
An exploitable uninitialized variable vulnerability exists in the RTF-parsing functionality of Atlantis Word Processor. A specially crafted RTF can leverage an uninitialized stack address, resulting in an out-of-bounds write. Detailed vulnerability information can be found here.
Tested versions: Atlantis Word Processor 3.0.2.3, 3.0.2.5
An exploitable out-of-bounds write vulnerability exists in the Word Document parser of Atlantis Word Processor. A specially crafted document can cause Atlantis to write a value outside the bounds of a heap allocation, resulting in a buffer overflow. An attacker must convince a victim to open a specially crafted, malicious document in order to trigger this vulnerability. Detailed vulnerability information can be found here.
Tested versions: Atlantis Word Processor 3.2.6
An exploitable arbitrary write vulnerability exists in the Word Document parser of Atlantis Word Processor. A specially crafted document can cause Atlantis to skip the addition of elements to an array that is indexed by a loop. When reading from this array, the application will use an out-of-bounds index, which can result in arbitrary data being read as a pointer. Later, when the application attempts to write to said pointer, an arbitrary write will occur. This can allow an attacker to further corrupt memory and execute code under the context of the application. An attacker must convince a victim to open a malicious document in order to trigger this vulnerability. Detailed vulnerability information can be found here.
Tested versions: Atlantis Word Processor 3.0.2.3, 3.0.2.5
An exploitable near-null write vulnerability exists in the Word Document parser of Atlantis Word Processor. A specially crafted document can cause an array to fetch a NULL pointer and then performs some arithmetic before writing a value to the result. Due to the application using the null pointer, there is arithmetic that can result in the pointer being larger than a few pages. This can corrupt heap memory, resulting in code execution under the context of the application. An attacker must convince a victim to open a document in order to trigger this vulnerability. Detailed vulnerability information can be found here.
Tested versions: Atlantis Word Processor 3.0.2.3, 3.0.2.5
An exploitable uninitialized length vulnerability exists within the Word Document parser of Atlantis Word Processor. A specially crafted document can cause Atlantis to skip initializing a value representing the number of columns of a table. Later, the application will use this as a length within a loop that will write to a pointer on the heap. A buffer overflow will occur due to this value being controlled, which can lead to code execution under the context of the application. An attacker must convince a victim to open a document in order to trigger this vulnerability. Detailed vulnerability information can be found here.
Tested versions: Atlantis Word Processor 3.0.2.3, 3.0.2.5
An exploitable heap-based buffer overflow vulnerability exists in the Windows Enhanced Metafile parser of Atlantis Word Processor. A specially crafted image embedded within a document can cause an undersized allocation, resulting in an overflow when the application tries to read data into it. An attacker must convince a victim to open a malicious document in order to trigger this vulnerability. Detailed vulnerability information can be found here.
Tested versions: Atlantis Word Processor 3.2.5.0
An exploitable heap-based buffer overflow vulnerability exists in the JPEG parser of Atlantis Word Processor. A specially crafted image embedded within a document can cause a length to be underflowed, which is then treated as unsigned. Later, when using this length in a copying operation, the application will write outside the bounds of a heap-buffer resulting in a buffer overflow. An attacker must convince a victim to open a malicious document in order to trigger this vulnerability. Detailed vulnerability information can be found here.
Tested versions: Atlantis Word Processor 3.2.5.0
An exploitable double-free vulnerability exists in the Office Open XML parser of Atlantis Word Processor. A specially crafted document can cause a TTableRow instance to be referenced twice, resulting in a double-free vulnerability when both the references go out of scope. An attacker must convince a victim to open a malicious document in order to trigger this vulnerability. Detailed vulnerability information can be found here.
Tested versions: Atlantis Word Processor 3.2.5.0
The following Snort rules will detect exploitation attempts. Note that additional rules may be released at a future date, and current rules are subject to change, pending additional vulnerability information. For the most current rule information, please refer to your Firepower Management Center or Snort.org.
Snort Rules: 47403 - 47412, 47456 - 47457, 47527 - 47528, 47523 - 47524, 47521 - 47522, 47758 - 47760, 47755 - 47756, 47762 - 47763
![]()
Overview
Cisco Talos is disclosing several vulnerabilities discovered in Atlantis Word Processor. Atlantis Word Processor is a portable word processor that is also capable of converting any TXT, RTF, ODT, DOC, WRI, or DOCX document into an eBook in the ePub format.
TALOS-2018-0641 - Atlantis Word Processor Uninitialized TDocOleObject Code Execution Vulnerability (CVE-2018-3975)
An exploitable uninitialized variable vulnerability exists in the RTF-parsing functionality of Atlantis Word Processor. A specially crafted RTF can leverage an uninitialized stack address, resulting in an out-of-bounds write. Detailed vulnerability information can be found here.
Tested versions: Atlantis Word Processor 3.0.2.3, 3.0.2.5
TALOS-2018-0646 - Atlantis Word Processor Word Document Complex Piece Descriptor Table Fc.Compressed Code Execution Vulnerability (CVE-2018-3978)
An exploitable out-of-bounds write vulnerability exists in the Word Document parser of Atlantis Word Processor. A specially crafted document can cause Atlantis to write a value outside the bounds of a heap allocation, resulting in a buffer overflow. An attacker must convince a victim to open a specially crafted, malicious document in order to trigger this vulnerability. Detailed vulnerability information can be found here.
Tested versions: Atlantis Word Processor 3.2.6
TALOS-2018-0650 - Atlantis Word Processor Word Document Endnote Reference Code Execution Vulnerability (CVE-2018-3982)
An exploitable arbitrary write vulnerability exists in the Word Document parser of Atlantis Word Processor. A specially crafted document can cause Atlantis to skip the addition of elements to an array that is indexed by a loop. When reading from this array, the application will use an out-of-bounds index, which can result in arbitrary data being read as a pointer. Later, when the application attempts to write to said pointer, an arbitrary write will occur. This can allow an attacker to further corrupt memory and execute code under the context of the application. An attacker must convince a victim to open a malicious document in order to trigger this vulnerability. Detailed vulnerability information can be found here.
Tested versions: Atlantis Word Processor 3.0.2.3, 3.0.2.5
TALOS-2018-0651 - Atlantis Word Processor Empty TTableRow TList Code Execution Vulnerability (CVE-2018-3983)
An exploitable near-null write vulnerability exists in the Word Document parser of Atlantis Word Processor. A specially crafted document can cause an array to fetch a NULL pointer and then performs some arithmetic before writing a value to the result. Due to the application using the null pointer, there is arithmetic that can result in the pointer being larger than a few pages. This can corrupt heap memory, resulting in code execution under the context of the application. An attacker must convince a victim to open a document in order to trigger this vulnerability. Detailed vulnerability information can be found here.
Tested versions: Atlantis Word Processor 3.0.2.3, 3.0.2.5
TALOS-2018-0652 - Atlantis Word Processor Word Document Paragraph Property (0xD608) sprmTDefTable Uninitialized Length Code Execution Vulnerability (CVE-2018-3984)
An exploitable uninitialized length vulnerability exists within the Word Document parser of Atlantis Word Processor. A specially crafted document can cause Atlantis to skip initializing a value representing the number of columns of a table. Later, the application will use this as a length within a loop that will write to a pointer on the heap. A buffer overflow will occur due to this value being controlled, which can lead to code execution under the context of the application. An attacker must convince a victim to open a document in order to trigger this vulnerability. Detailed vulnerability information can be found here.
Tested versions: Atlantis Word Processor 3.0.2.3, 3.0.2.5
TALOS-2018-0666 - Atlantis Word Processor Windows Enhanced Metafile Code Execution Vulnerability (CVE-2018-3998)
An exploitable heap-based buffer overflow vulnerability exists in the Windows Enhanced Metafile parser of Atlantis Word Processor. A specially crafted image embedded within a document can cause an undersized allocation, resulting in an overflow when the application tries to read data into it. An attacker must convince a victim to open a malicious document in order to trigger this vulnerability. Detailed vulnerability information can be found here.
Tested versions: Atlantis Word Processor 3.2.5.0
TALOS-2018-0667 - Atlantis Word Processor JPEG Length Underflow Code Execution Vulnerability (CVE-2018-3999)
An exploitable heap-based buffer overflow vulnerability exists in the JPEG parser of Atlantis Word Processor. A specially crafted image embedded within a document can cause a length to be underflowed, which is then treated as unsigned. Later, when using this length in a copying operation, the application will write outside the bounds of a heap-buffer resulting in a buffer overflow. An attacker must convince a victim to open a malicious document in order to trigger this vulnerability. Detailed vulnerability information can be found here.
Tested versions: Atlantis Word Processor 3.2.5.0
TALOS-2018-0668 - Atlantis Word Processor Office Open XML TTableRow Double Free Code Execution Vulnerability (CVE-2018-4000)
An exploitable double-free vulnerability exists in the Office Open XML parser of Atlantis Word Processor. A specially crafted document can cause a TTableRow instance to be referenced twice, resulting in a double-free vulnerability when both the references go out of scope. An attacker must convince a victim to open a malicious document in order to trigger this vulnerability. Detailed vulnerability information can be found here.
Tested versions: Atlantis Word Processor 3.2.5.0
Coverage
The following Snort rules will detect exploitation attempts. Note that additional rules may be released at a future date, and current rules are subject to change, pending additional vulnerability information. For the most current rule information, please refer to your Firepower Management Center or Snort.org.
Snort Rules: 47403 - 47412, 47456 - 47457, 47527 - 47528, 47523 - 47524, 47521 - 47522, 47758 - 47760, 47755 - 47756, 47762 - 47763